场景简介
对于在「无边界和数字世界」中竞争的企业来说,保护敏感系统和客户机密数据则至关重要。然而,当下的网络安全状况却并不乐观。当客户数据因为企业的维护不当而被滥用或窃取时,企业不仅会蒙受业务损失,甚至有可能还要面临巨额的合规罚款以及其他法律处罚。
根据 2016-2019 年的数据显示,中国企业 IT 支出占全球比重和 GDP 相对比来看,中国企业的数字化程度正处在高速增长中。当企业逐渐从 2020 的全球疫情影响中恢复过来时,他们也将面临大量的 IT 项目积压,然而,用于完成这些项目的资金却是有限的。
因此,建设身份云 IDaaS 将帮助企业更快实现数字化转型,减轻财务负担,也能有效避免给企业发展制造障碍增加不必要的成本。
Authing 已帮助 30000+ 家企业和开发者构建标准化的用户身份体系
完善的身份服务
传统 IAM 账号中心的运营能力较弱,难以满足大型组织在业务方面的需求,而 IDaaS 的多租户运营平台和自动化工作流(Workflow)则可以便捷地提升企业运营效率。
降低企业开发成本
订阅 Authing 将节约构建身份管理系统的成本,并减轻未来维修升级的负担。解放出来的人力物力可让开发团队专注于核心业务,为企业的创新能力开发出新的增长空间,也加快产品交付上市的时间。
提升运营管理效率
大型企业和组织的内部通常会根据“地域”、“部门”等维度进行业务划分,不同业务通常需要保证独立性,Authing 身份云利用多租户技术帮助企业解决业务和数据的隔离问题。
提升身份安全
动态令牌,人脸识别等多因素认证(MFA)功能,提高系统访问安全,保障用户访问安全。
提高系统的可扩展性
一旦购买身份管理 API 开发包,开发团队可在平台上对所需开发的应用进行集成,无需重复构建、购买身份管理方案,对开发者十分友好。
标准身份云需要包含的功能清单
以下是一套标准的身份云 IDaaS 需要包含的功能清单,当然,每一个企业都有自己独有的组织形式和业务模式。
一级功能
二级功能
说明
统一账户
用户管理
用户批量导入、导出
用户帐号的逐条/批量的增/删/改/查
用户属性管理(基础字段+自定义字段)
用户状态管理(启用/解锁/停用/激活等)
用户密码重置
组织管理
多级组织架构树
组织管理
用户组管理
用户组创建/查询/删除等
用户组属性管理
目录同步
账户同步(上游同步)
统一认证
认证源管理
支持认证源配置,支持添加企业微信、AD 认证源、LDAP 认证源;支持自定义认证源,包括基于 OpenID、SAML、CAS 协议的认证源
认证方式
支持多因子认证,包括账户名/密码、OTP、二维码、社交登录认证等
认证配置
支持针对不同的应用配置不同的认证因子
统一应用
应用管理
支持应用预集成;支持创建自定义应用(OpenId Connect、FormPost、SAML2.0、CAS、OIDC 等标准协议)
单点登录
支持为应用配置单点登录 SSO
账号供给
支持将账号、机构等同步到应用系统
SaaS 服务接入能力
支持通过 OIDC、SAML、CAS、LDAP、AD 等标准协议集成第三方 SaaS 或企业自建应用
租户级别应用接入能力
支持根据 IDaaS 身份云的不同租户接入不同应用
工作台集成
支持企业微信工作台;支持添加工作台
统一权限
权限管理
支持应用级授权;支持基于 RBAC 的授权
权限配置
支持基于用户/用户组/机构等授权
权限同步
支持应用权限的同步
统一审计
用户操作日志
支持用户操作日志的查询、导出
管理员操作日志
支持管理员操作日志的查询、导出
安全管理
管理员配置
支持管理员/管理员组的创建、删除等;支持配置不同管理员角色
安全策略
支持密码策略配置,包括密码强度设置、密码重置设置、登录安全设置等
多租户运营管理及运维能力
IDaaS 租户运营平台
企业运营中心支持对身份云内的所有租户、应用、订单等进行集中管理;核心数据可视化
IDaaS 运维平台
一键部署属 IDaaS 平台,系统运维、数据监控、服务升级尽在掌控
统一账户
用户管理
用户批量导入、导出
用户帐号的逐条/批量的增/删/改/查
用户属性管理(基础字段+自定义字段)
用户状态管理(启用/解锁/停用/激活等)
用户密码重置
组织管理
多级组织架构树
组织管理
用户组管理
用户组创建/查询/删除等
用户组属性管理
目录同步
账户同步(上游同步)
统一认证
认证源管理
支持认证源配置,支持添加企业微信、AD 认证源、LDAP 认证源;支持自定义认证源,包括基于 OpenID、SAML、CAS 协议的认证源
认证方式
支持多因子认证,包括账户名/密码、OTP、二维码、社交登录认证等
认证配置
支持针对不同的应用配置不同的认证因子
统一应用
应用管理
支持应用预集成;支持创建自定义应用(OpenId Connect、FormPost、SAML2.0、CAS、OIDC 等标准协议)
单点登录
支持为应用配置单点登录 SSO
账号供给
支持将账号、机构等同步到应用系统
SaaS 服务接入能力
支持通过 OIDC、SAML、CAS、LDAP、AD 等标准协议集成第三方 SaaS 或企业自建应用
租户级别应用接入能力
支持根据 IDaaS 身份云的不同租户接入不同应用
工作台集成
支持企业微信工作台;支持添加工作台
统一权限
权限管理
支持应用级授权;支持基于 RBAC 的授权
权限配置
支持基于用户/用户组/机构等授权
权限同步
支持应用权限的同步
统一审计
用户操作日志
支持用户操作日志的查询、导出
管理员操作日志
支持管理员操作日志的查询、导出
安全管理
管理员配置
支持管理员/管理员组的创建、删除等;支持配置不同管理员角色
安全策略
支持密码策略配置,包括密码强度设置、密码重置设置、登录安全设置等
多租户运营管理及运维能力
IDaaS 租户运营平台
企业运营中心支持对身份云内的所有租户、应用、订单等进行集中管理;核心数据可视化
IDaaS 运维平台
一键部署属 IDaaS 平台,系统运维、数据监控、服务升级尽在掌控
Authing 如何支持各种场景
API 安全
在零信任环境中提高 API 安全性并确保内部和外部合作伙伴用例的合规性可能非常具有挑战性。Authing 基于开放标准的方法提供端到端的 API 安全和管理。
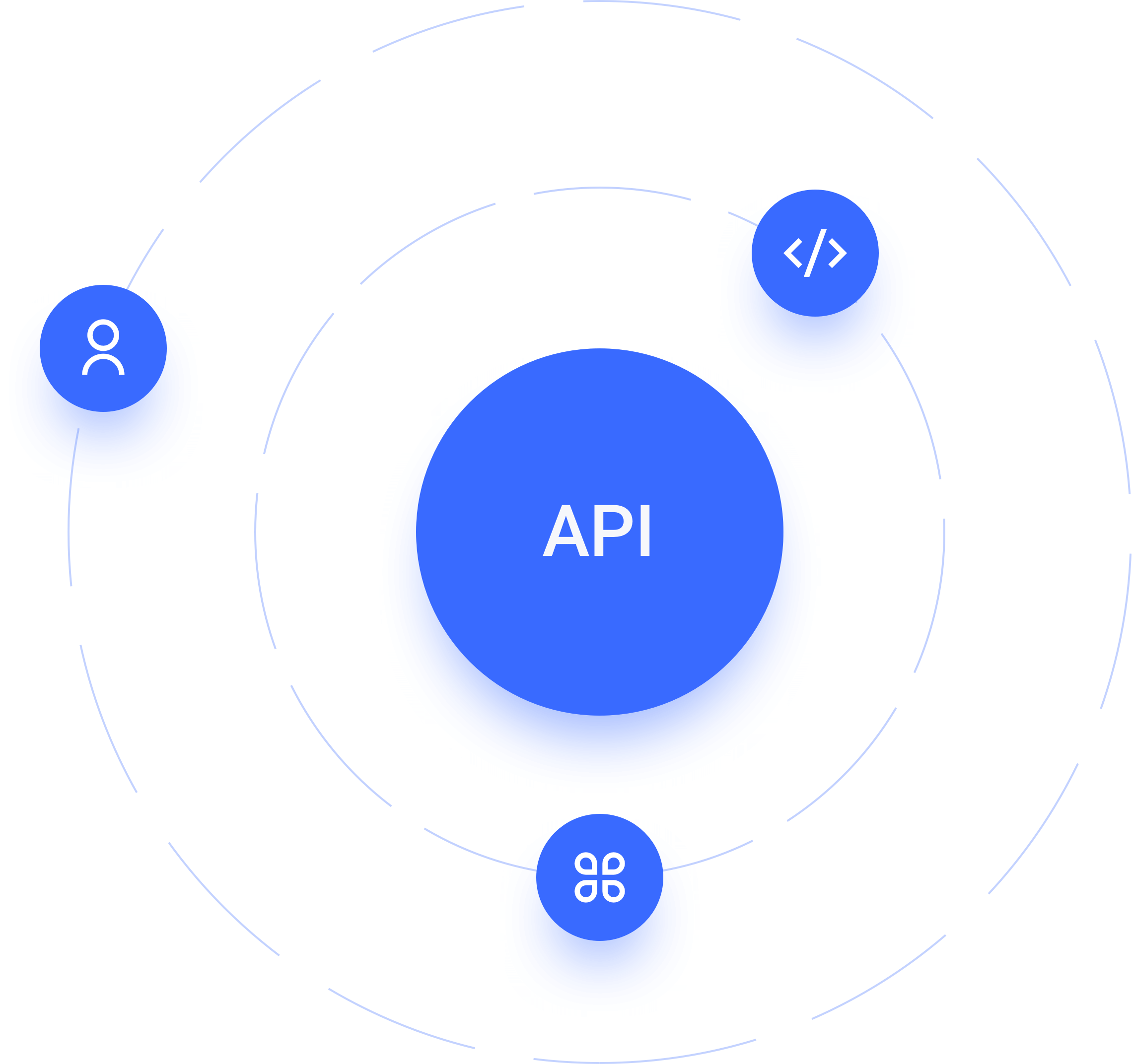
对于用户
通过支持所有 OAuth 2.0 授权流以及细粒度的范围和权限,轻松保护和公开您的 API,从而扩大市场范围并提供更好的用户体验。
对于应用和系统
只需轻按一下开关,即可轻松促进 API 与非交互式外部客户端以及内部 API 之间的安全通信。
对于企业开发者
使第三方应用服务器、API 和系统后端能够向您的 API 发出经过身份验证的请求,同时始终保持对精细范围和权限的控制。
众多合规认证,保障身份安全

毋庸置疑,客户数据安全性和合规性是大多数公司的首要考虑因素。Authing 在产品中内置了先进的安全性,因此您无需为您的用户和业务安全忧虑。
行业标准协议:通过采用支持 OAuth 和 OpenID Connect 等行业认证标准的身份平台,提高业务运营和执行的一致性和连续性。
合规性和认证:Authing 拥有多项国内国际合规认证,包括国家三级等保、SOC 2、GDPR、ISO 9001、CCPA、PCI、HIPAA 和 FERPA 等,誓要保障每一位用户、每一个业务的安全。
公共和私有云:在 Authing 的公共云、我们的私有云或您的 AWS 环境中托管您的应用。我们高度可用的多租户云服务每天可以处理大量交易。
快速集成 五分钟实现
单点登录、认证授权、权限管理等功能