Scene profile
Traditional IAM is not from the heart in internal employee management and external user management; It is not flexible when new applications and compatible old applications. At the same time, the IdaAs service that came out of the air has replaced the traditional IAM into enterprise infrastructure due to the extension advantage and cross-environment identification and authority management capabilities.
Authing Value
IDaaS is an abbreviation of Identity As a Service. Contains all functions of traditional IAM and can bring more benefits to companies: enhance marketing and operational efficiency; Accelerate new business online; enhance safety to reduce network attack risks; enhance user experience.
Operation capacity
The traditional IAM account center has weak operational capabilities, difficult to meet large organizations in business, while IDaaS's multi-tenant operation platform and automation workflow (Workflow) can easily enhance corporate operation efficiency.

How Authing support various scenarios
API security
Improving API security and ensuring compliance with internal and external partner use cases in a zero trust environment can be challenging. Authing provides end-to-end API security and management based on an open standards approach.
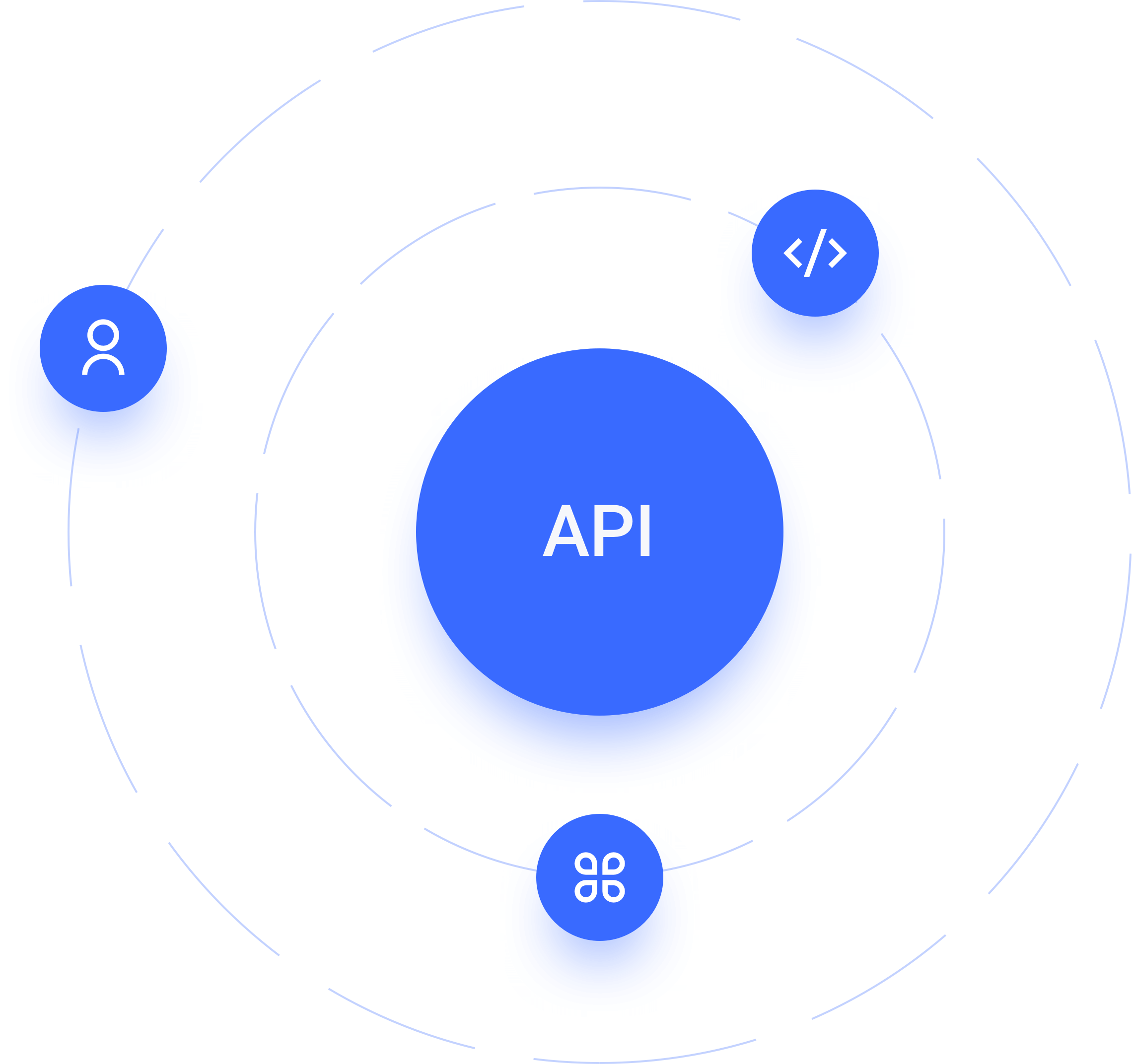
For users
Easily protect and expose your API by supporting all OAuth 2.0 authorization flows and fine-grained scope and permissions, so as to expand the market scope and provide a better user experience.
For applications and systems
You can easily facilitate secure communication between the API and non interactive external clients and internal APIs with the touch of a switch.
For enterprise developers
Enable third-party application servers, APIs and system backend to issue authenticated requests to your APIs, while always maintaining control over fine scope and permissions.
Numerous compliance certifications to ensure identity security

There is no doubt that customer data security and compliance are the primary considerations of most companies. Authing has the most advanced security built into the product, so you don't have to worry about the security of your users and business.
Industry standard agreement: Improve the consistency and continuity of business operation and execution by adopting identity platforms that support industry certification standards such as OAuth and openid connect.
Compliance and certification: Authing has a number of domestic and international compliance certifications, including the DJCP Level 3, SOC 2, GDPR, ISO 9001, CCPA, PCI, HIPAA and FERPA, etc., vowing to protect every user & business.
Public and private clouds: Host your application in authoring's public cloud, our private cloud or your AWS environment. Our highly available multi tenant cloud service can handle a large number of transactions every day.
Learn more
Universal Login
The guard helps developers shield themselves from many of the implementation...
Mobile Number Verification
Relying on the official real name user information of wechat, users can...
Custom Database Connection
When you want to ensure data security or smooth migration of users, please use Authing...
Integrate Authing in 5 minutes
Single sign-on, authentication, authorization management, etc.